Cybersecurity: How Utilities of All Sizes Can Take Action to Keep their Systems Safe

If a hacker gets his hands on your Kohl’s charge information, it’s a real headache. But if that hacker taps into your community’s water or wastewater system, it becomes a problem on a whole other level.
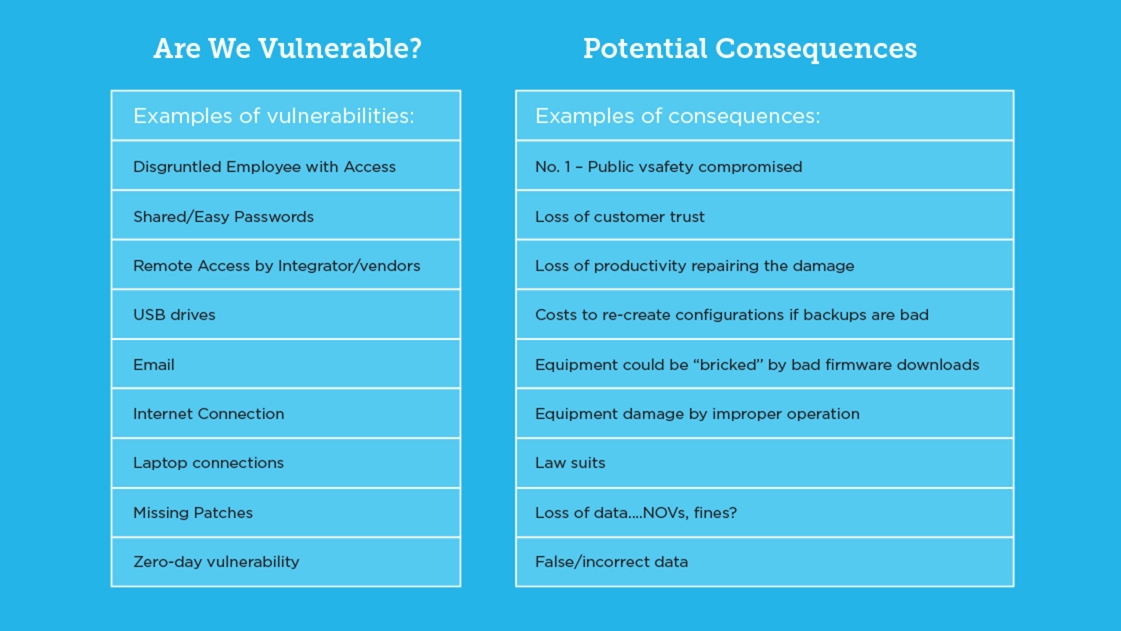
As advanced cyberattacks are on the rise worldwide, those responsible for public utilities need to be aware of the risks and what can be done to mitigate them. The U.S. Department of Homeland Security considers water systems to be critical infrastructure. It is entirely possible that cyberterrorists could target vulnerabilities in our water and wastewater systems in the U.S.—and not just when they are connected to the internet. If laptops, USB drives, or other removable media are exposed to malware, then brought inside your firewall, it can put you at risk. So can something as seemingly innocent as using a cellphone to take a reading.
The impact of a water or wastewater system being compromised is significant, often to a much greater degree than compromising a business network. For a company, an attack can cost a lot of money. But with a water utility, if someone takes control of the network, it’s not just money at stake—it’s people’s health.
That’s why major utilities such as Great Lakes Water Authority (GLWA), which serves a customer base of more than 3.9 million people, put so much effort into keeping their information systems—specifically the industrial control network or the process network—safe from outside intrusion. They strive to maintain the integrity of their systems and ensure they remain available to the people who rely on them every day by taking actions such as eliminating remote access to the network and putting security measures in place.
A terrific resource to help utilities get a better grasp of the issues and start putting an action plan in place is the American Water Work Association. Not only do they offer an online tool to address Presidential Executive Order No. 13636 mandating improvements to critical infrastructure cybersecurity, which was signed by President Obama on Feb. 12, 2013, they also offer training for how to use the tool.
To share with you some additional insight into the issue and why it’s so important for utilities to increase their understanding of cybersecurity risks and to take advantage of resources that exist to help, we’ve prepared this Q&A with David Manor, Director of IT Security and Risk Management for GLWA:
1. In your opinion, are our country’s utilities positioned to address cybersecurity issues? And if not, what are the barriers?
I think that basic principles are understood in most cases. But there can be challenges in addressing those principles and placing a priority on cybersecurity. In some cases, it’s a money issue. Especially for smaller utilities, there may not be budget for a full time CISO, or Chief Information Security Officer. Money aside, smaller utilities with fewer systems simply might not have the need or the workload to keep a CISO busy full-time.
2. So, what steps can a utility take to address cybersecurity in the absence of a full-time CISO?
There are some basic things that utilities can do that can eliminate a major percentage of their risk, and many can be done by a sharp desktop support person. Things like making sure all the systems are patched at least one a month and making sure there is endpoint protection in place, beyond antivirus, to avoid network breaches that might come from security weak points, such as tablets, smartphones, and other wireless devices that may not be protected. Laptops and other mobile devices need to have protection for when they are outside of network, and this is fairly easy to do. For example, here are some helpful tips to smartphones.
For utilities that don’t have these capabilities in house, some states—Michigan for example—offer CISO-as-a-service where utilities can essentially get part-time help from a qualified IT professional. Communities receive a scorecard or assessment they can use to better understand and prioritize their risks. This scorecard leverages the state’s free CySAFE IT assessment tool.
The Department of Homeland Security also offers services to help organizations prevent attacks by understanding their IT landscape, identifying their most critical needs, and creating plans to address them.
One thing utilities must keep in mind, however, is that cybersecurity is an ongoing process. They need to continually review their needs and make updates to keep their cybersecurity plans up to date. It’s not just a one-and-done type of endeavor.
3. What system vulnerabilities are most often overlooked or misunderstood?
The most overlooked are often the most obvious, and fairly straightforward to remediate. Things like perimeter defense, such as firewalls and instruction detection, operating system patching and application patching, and endpoint protection including antivirus, firewalls, and intrusion detection on the endpoints. Also, segregating your industrial control network so that it cannot be accessed via the internet is a must.
People tend to think these things are too difficult or too expensive to implement, and they’re not. They can often be addressed by an in-house IT support person or a CISO-as-a-service resource. Utilities can also sign up for services that alert them to vulnerabilities and patches. There are several options available. The danger here, however, is information overload. Utilities will need someone to filter through the information and identify the priority issues. But if each of these items are checked off the list, most utilities will be in fairly decent shape.
Of course, you also need to watch out for those emails that trick employees into clicking a link, and viola, the hacker has access to your system. This is a bit trickier. But the key here is employee education. There are free “phishing” training tools available online.
4. If there’s one thing utilities need to internalize about cybersecurity, what would it be?
It is possible to have a good IT security program, regardless of the size of the water utility. Perhaps it’s just a word document that outlines what you do every day, every week, and every month. And that’s perfectly acceptable for smaller utilities. The key is to stay informed and to take the reasonable measures—patching, endpoint protection, and network segregation—to protect your infrastructure. And there’s help out there. With the excellent programs available from the Department of Homeland Security, the AWWA’s cybersecurity tool and guidance, and the CySAFE program, cybersecurity is in reach for all utilities.
As cybersecurity threats increase, it’s best to practice vigilance
As the community advancement firm, OHM Advisors wants every community to have access to the critical information they need to optimize and protect the infrastructure that provides the best possible quality of life. We’re pleased to partner with the Great Lakes Water Authority to share this valuable information.